A customer send out the request to take a look at a few alarms they received in the NSX Manager console. The alarm they received was about a expiring certificate for local manager.
A customer send out the request to take a look at a few alarms they received in the NSX Manager console. The alarm they received was about a expiring certificate for local manager.
We did some investigating from the NSX Manager and it was clear that this was a self-signed (not linked to the company own PKI infrastructure) and it was in use. This last comment means we have to use the Application Programing Interface (API) to tell NSX to use the new certificate.
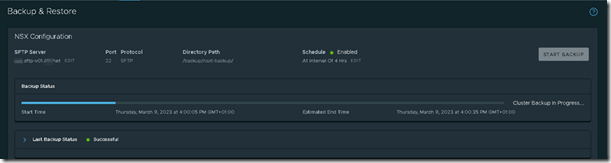
Since this is a production environment we don’t do anything before we have verified that a recent backup of the NSX database is available. Please take note that a VMware snapshot is not supported the restore a NSX Manager Cluster. It is best practice to have a scheduled NSX Manager backup schedule. Before we start working on the environment we create a manual backup of the NSX database.
When we have verified that we have a recent backup we move to the certificate node (Click system > click certificates > click the certificates tab) to verify which certificate we need to update.
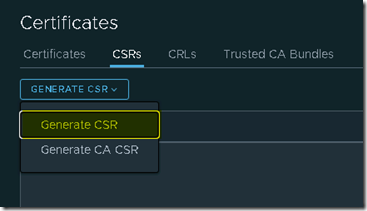
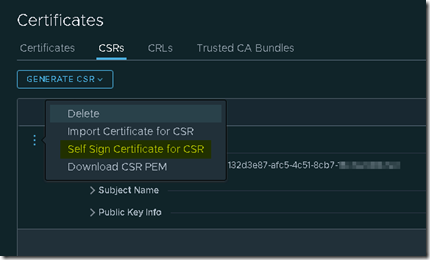
Under certificates we move to the tab CSR and select Generate CSR> Generate CSR.
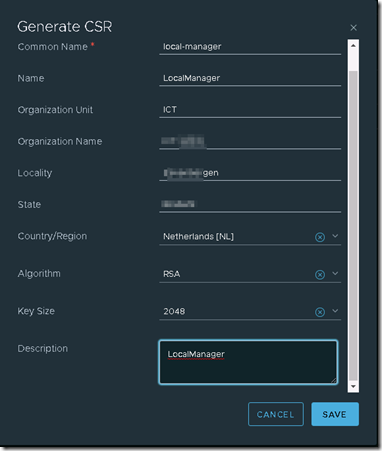
In the following screen we need to collect data for the new certificate.
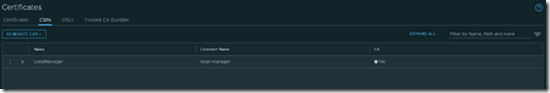
Under the tab CSR we see our new request.
By selecting this line we choose Self Sign Certificate for CSR from the context menu.
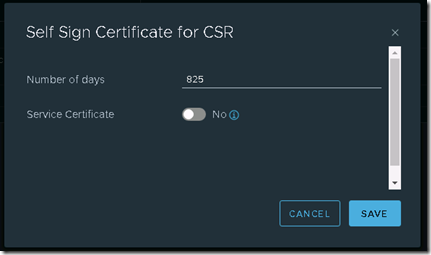
In the following window we can choose how long the certificate is valid and indicate if this is a service certificate (which it is not).
The certificate is now created, but we are not finished we have to tell NSX to use the new certificate. To create the API calls to configure this we need the have the certificate ID.
We are able to locate this information from the NSX Manager UI.
For the next phase we need Postman.
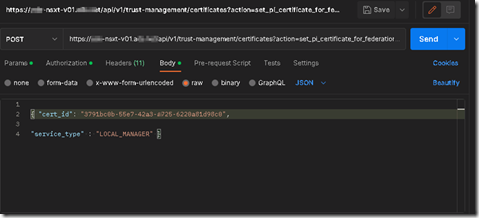
Create the following command:
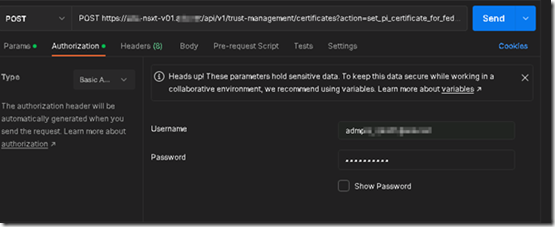
POST https://<nsx-mgr.fqdn>/api/v1/trust-management/certificates?action=set_pi_certificate_for_federation
Enter your credentials for the NSX Manager on the authorization tab.
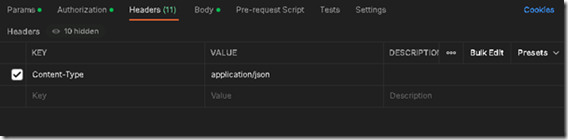
On tab header add key Content-Type, with value application/json
On tab Body, choose raw and select format JSON
Add the folowing lines
{ “cert_id”: “<id>”,
“service_type”: “LOCAL_MANAGER” }
Now you are ready to click send. If you entered everything correctly you will see the following message: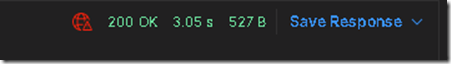
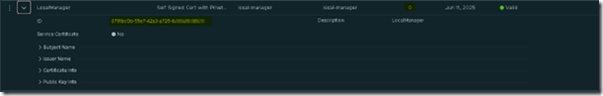
Next we return to the certificate node. Notice that the new certificate is valid and in use.
You can now remove the expired certificate.